DayDayMap is a SaaS service platform that provides comprehensive, precise, and real-time global network asset mapping services.

Creating realistic decoy environments for superior network security and threat detection
Contact WebRAY
-
 Business Network Simulation
Business Network SimulationThe system offers comprehensive simulation capabilities, supporting the emulation of various objects such as networks, devices, systems, databases, applications, services, and middleware. It supports distributed heterogeneous honeynets and enables high-fidelity multi-layer simulation of target business networks through website mirroring, system cloning, endpoint cloning, network traffic learning, and visual orchestration.
-
 Attack Behavior Capturing
Attack Behavior CapturingThe system actively captures attacks using techniques such as virtual IPs, traffic forwarding, and Trunk deployment. It supports automatic deployment of decoy markers (honey tokens) and integrates with network asset mapping, attack surface analysis, XDR alerts, and real-time attack dynamics data to automatically adapt and optimize the honeynet. Additionally, it can collaborate with gateway devices to actively redirect attack traffic for analysis and defense.
-
 Attack Detection and Analysis
Attack Detection and AnalysisThe system collects attack data comprehensively, using multiple engines like behavioral baselines, correlation analysis, signature matching, threat intelligence, and behavioral models to identify known and unknown threats or anomalies. It visualizes the full attack kill chain based on the ATT&CK framework, enabling a detailed reconstruction of the attack process.
-
 Attack Attribution and Forensics
Attack Attribution and ForensicsBy capturing attacker fingerprints, virtual identities, and attack methods, the system generates detailed attacker profiles. It supports attack behavior attribution, forensics, and active countermeasures like decoy poisoning to mislead or retaliate against attackers.
-
 Attack Response
Attack ResponseThe system supports comprehensive event analysis and handling, offering multiple alert notification methods and producing internal threat intelligence. It also integrates with third-party systems via APIs to provide layered threat response and mitigation, effectively blocking and neutralizing attacks.
-
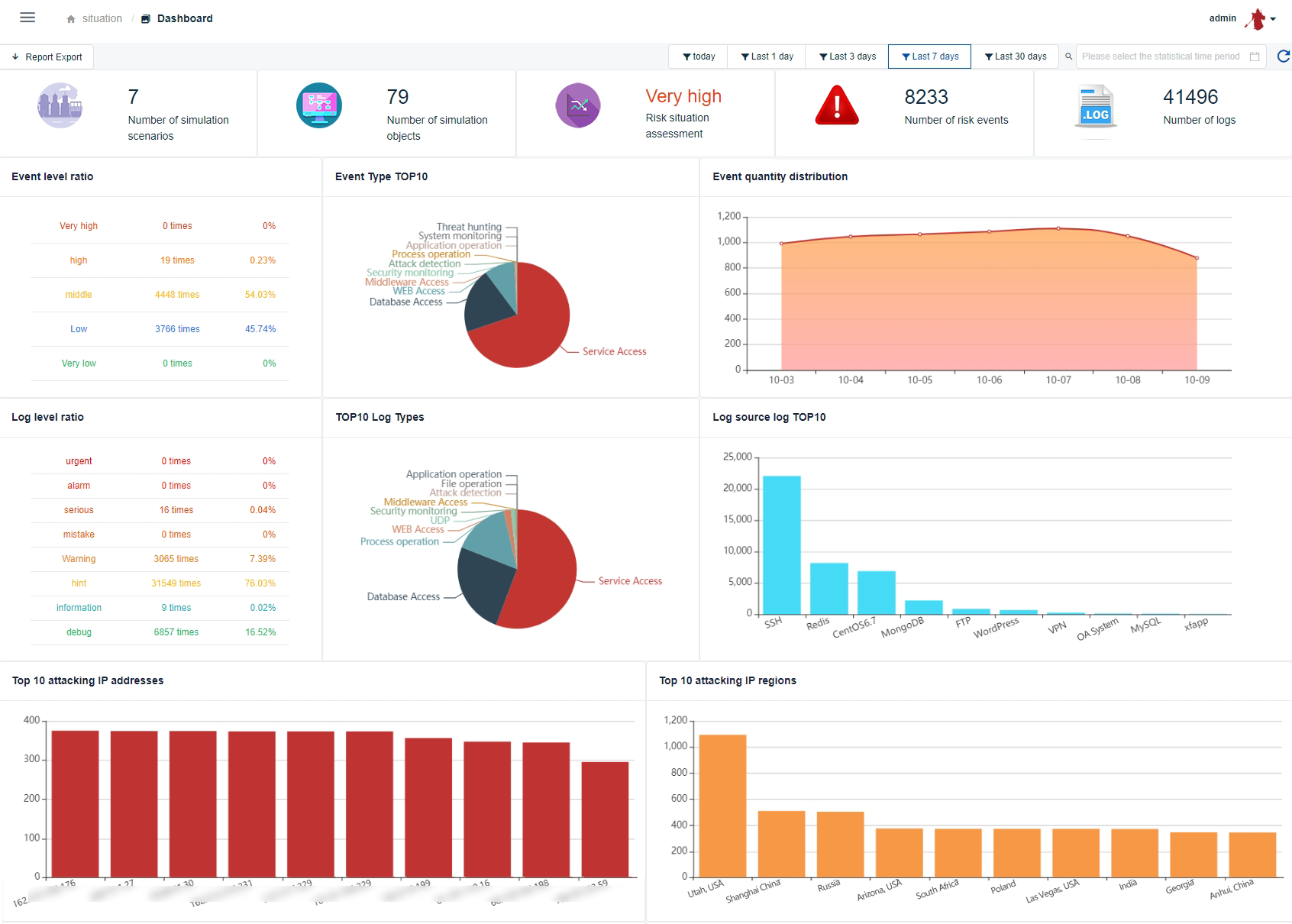
 Centralized Management
Centralized ManagementThe centralized management oversees distributed, hierarchical deployments, allowing unified management of honeypot data and risk events. It provides real-time insights into network attack, defense, and operational statuses using 3D visualization, offering a global perspective of network risk trends.

.png)